Cyber Incident Response
Are you ready?
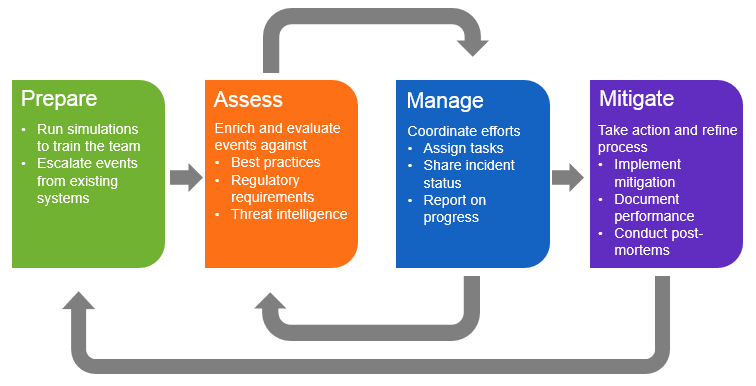
Cyber incidents will occur in your organization, it is only a matter of time. How you respond to those incidents will greatly increase or decrease the impact that these incidents have upon your company. It all starts by having a plan in place and practiced in your organization. Are you ready?
With the increased pervasiveness of cyber attacks, as well as their increased sophistication, we first must talk about monitoring so that you can be made aware of these incidents. With the proper technologies, processes, and people surrounding your organization, you will be able to provide adequate coverage for your organization now and into the future.
Now that you have the appropriate monitoring in place to alert you to attacks that are occuring, what's next? There are several key parts to an incident response plan, as noted by the McKinsey & Company article "How good is your cyberincident-response plan". They are the following:
- Incident Taxonomy
- Data-classification frameworks
- Performance objectives
- Definition of response-team operating models
- Identification and remediation of failure modes
- Key tools for use during response
Incident taxonomy details the lay out of your incident categorization. There are many standards available, including the National Institute of Standards and Technology (NIST) Special Publication 800-61R2. These basic categories are unauthorized access, malicious code, denial of service, and inappropriate usage. Giving an incident a category allows you to understand the actions that you need to take to remediate the incident.
Data-classification frameworks are used to identify the severity of the data which is being accessed. Many organizations utilize a four level classification system, ranging from public to restricted. This allows you to know the severity of the incident. If someone has broken into a database that contains public data, there is most likely less severity than with a database of level restricted. Having these data classifications clearly defined and cataloged will allow you to make the appropriate risk decisions in the moment.
Performance objects pertain to the response objectives that you have for each data classification which you defined in the previous paragraph. This is a guideline for all parties involved as to what their expected turnaround time is to respond to an incident of a specific data classification. Setting expectations and documenting them allows you to avoid any confusion and issues in training down the road.
Defining the composition and roles of the incident response team also helps to set expectations to involved parties as to what their expected participation involves. It also calls out escalation procedures and protocols which the incident response team will follow regarding any incident that they are involved in. Some of the questions this should answer are, when should I involve senior leadership in the incident? At what point should drastic measures be taken to remediate the incident at all cost? Who will contact law enforcement and when will they do it? These are all questions you need to document as part of your incident response process.
Identifying and remediating of failure modes is basically process improvement. You should evaluate each response and improve the process by using "lessons learned" and thoroughly discussing the pitfalls that might come up in your process. By constantly improving your process you can become more agile and responsive to incident which will come up.
Key tools for incident response will document all of the forms and templates for documenting the incident to all playbooks or checklists that will be necessary to thoroughly investigate and remediate an incident. This will change depending on the data classification, so you will need to call this out.
Do you see the benefits of planning your response to an incident now? There are many facets that you need to think of before an attack occurs so that you are prepared to remediate the issue, document the attack, and respond to the public in an informed manner, having taken the appropriate actiosn to establish trust in your brand and your process.
References
McKinsey & Company - How good is your cyberincident-response plan?Department of Homeland Security - National Cyber Incident Response Plan
Crest Approved - Cyber Security Incident Response Guide
National Institute of Standards and Technology - Special Publication 800-61R2
