Site Plan
Site Description
Site Name
byui.allthingsnetwork.org
Site Purpose
AllThingsNetwork.org will be a centralized repository for the network security professionals and managers to obtain summarized or detailed information regarding recent breaches/hacks, trending security architecture practices, and basic news/information in one centralized location.
Target Audience
- Who: Current and aspiring network security professionals and managers
- Age: Most will range from 20 to 60 years of age.
- Technology: Modern, typically a laptop less than four years old, most will also carry a tablet and/or smartphone. Their browsers are up-to-date, but the browser type will differ widely.
- Education: Associates to Doctorate level college education with varying technical certificates.
- Income: Income levels will typically be between $50,000 and $200,000 annually.
- Motivation: Security professionals are always searching for valid, current, and concise information regarding security vulnerabilities and architectures. Their motivation will be to find as few sites as possible to stay current on the topic of network security.
Personas

- Occupation: Security Operations Technician
- Demographics: 27 years old, technician for a large multinational bank.
- Goals: Seeks to enter an engineering or management roll in his current company and wants to know more about security globally.
- Social: Avid Twitter fan, and uses Facebook regularly as well.
- Technology: Uses his work laptop, but mostly uses his tablet and mobile phone for personal use.
- Quote:
Network security is such a new realm to me and knowing the basics is essential to my success.

- Occupation: Chief Information Security Officer
- Demographics: 42 years old, CISO of a medium sized company.
- Goals: Understand the architectures and products needed for a company to successfully protect it's assets.
- Social: Rarely uses any social media, but uses Facebook to keep up with family.
- Technology: Her laptop is her go to technology device. Her phone is only for emails and phone calls.
- Quote:
What technologies should I be implementing to protect my business?

- Occupation: Network Security Engineer
- Demographics: 45 years old, engineer for a multitenant data center provider.
- Goals: Looking to keep abreast of all new security events globally.
- Social: Uses Facebook avidly, but also uses technology forums.
- Technology: Uses his laptop for work related activities, but his tablet is his main personal device.
- Quote:
Keeping up with all the security initiatives and issues around the world is almost impossible.
Scenarios
- What have been the most recent breaches and how did they occur?
- What are trending technologies that will improve my security posture?
- How do I stay current on best practices?
- How do I stay current on the current cybercrime news?
- How should I protect the privacy of my customers information?
- What regulations are established that I must adhere to?
- How should cloud security be approached while still providing flexibility?
- What BYOD policies are being used in corporations today?
- How do I provide the appropriate training and motivation for my employees regarding security?
- How best should I protect from insider threats?
Content Architecture
- What have been the most recent breaches and how did they occur?
-
- Text explaining the three most recent data breaches and the vulnerabilities used.
- Links to a chronological list of breaches.
- What are trending technologies that will improve my security posture?
-
- Text explaining the current technologies and why they are trending.
- Links to detailed information regarding the Gartner Quadrant major players for each trending technology.
- Audio files or podcasts from authoritative sources describing trending technologies and why they are important.
- Infographic of top technologies that should be implemented for a successful security program.
- Is security awareness training affective?
-
- Text explaining the purpose behind security awareness training and how it helps your overall security posture.
- Links to multiple sites that are references for security awareness training.
- Audio podcast discussing the multiple facets of security awareness training.
- What are affective policies that I should establish in my organization?
-
- Text describing a baseline policies and standards that should be established in every organization and their benefits.
- Links to multiple sites that can help you develop your own policies and standards.
- How should I protect the privacy of my customers information?
-
- Text defining privacy policy on a global scale and the methods used to support privacy.
- Links to supporting sites for global privacy policies and standards.
- What regulations are established that I must adhere to?
-
- Text defining current major regulations and which governments are requiring them.
- Text defining what activities are covered under specific regulations and how to comply with them.
- Links to supporting documentation on government websites.
- How should cloud security be approached while still providing flexibility?
-
- Text defining what the cloud is and why businesses are seeking it's services.
- Text explaining how security should be approached for such an environment as to provide security but retain flexibility.
- Links to supporting documentation, policies, and best practices.
- What BYOD policies are being used in corporations today?
-
- Text explaining why BYOD has become so popular and why it is a risk in corporate society today.
- Text demonstrating implemented policies which are working well for small to large scale companies.
- Links to support documentation, policies, and best practices.
- How do I provide the appropriate training and motivation for my employees regarding security?
-
- Text explaining the importance of security training for the entire corporate community.
- Text demonstrating the type of training required at each level of the corporate community.
- Links to examples of training in corporations
- How best should I protect from insider threats?
-
- Text demonstrating recent examples of insider threats in the news.
- Text explaining best practices and policies for mitigating insider threats.
- Links to supporting documentation, policies, and best practices.
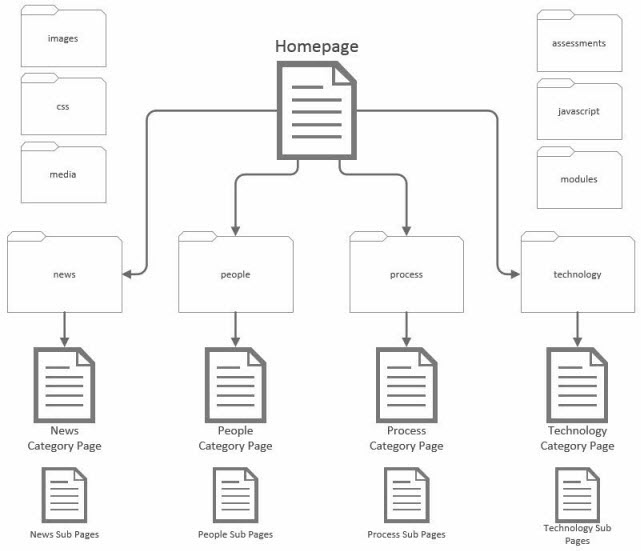
Site Map
Style Guide
Color Scheme
The color scheme is based off of the logo to keep the website cohesive and flowing. The #FEFEFE color will be used for my background. The rest will be utilized in the typography and content blocks.
| Color HEX & RGB | Example |
|---|---|
| #474759 R:71 G:71 B:89 |
|
| #B63A42 R:182 G:58 B:66 |
|
| #FEFEFE R:254 G:254 B:254 |
|
| #D6D1D5 R:214 G:209 B:213 |
|
| #E88994 R:232 G:137 B:148 |
Below is the logo for the site that I will be utilizing for my brand.

Typography
Arial will be the primary font with Helvetica used for all heading levels.
| Text Requirements | Example |
|---|---|
| Default body text 16px Arial, Verdana, sans-serif #474759 |
Default body text |
| Site level - Heading Level 1 (H1) 48px Open Sans, Arial, sans-serif #868185 |
Site Level H1 |
| Primary Navigation 20px Open Sans, Arial, sans-serif #B63A42 |
Primary Navigation |
| Heading Level 1 (H1) 36px Open Sans, Arial, sans-serif #B63A42 |
Heading Level 1 |
| Heading Level 2 (H2) 28px Open Sans, Arial, sans-serif #E88994 |
Heading Level 2 |
| Heading Level 3 (H3) 22px Open Sans, Arial, sans-serif #868185 |
Heading Level 3 |
| Heading Level 4-6 (H4-6) 18px Open Sans, Arial, sans-serif #868185 |
Heading Level 4-6 |
| Footer text 16px Arial, Verdana, sans-serif #E88994 |
Footer text |
Navigation
The navigation menu system below will be placed at the bottom of the header area, which will be above the main content. This will be restricted to roughly 800 pixels. The navigation will be identical for the entire website.

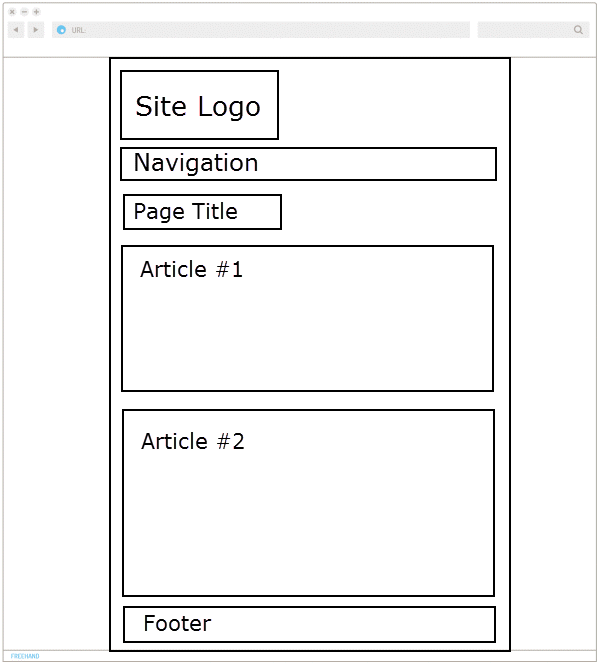
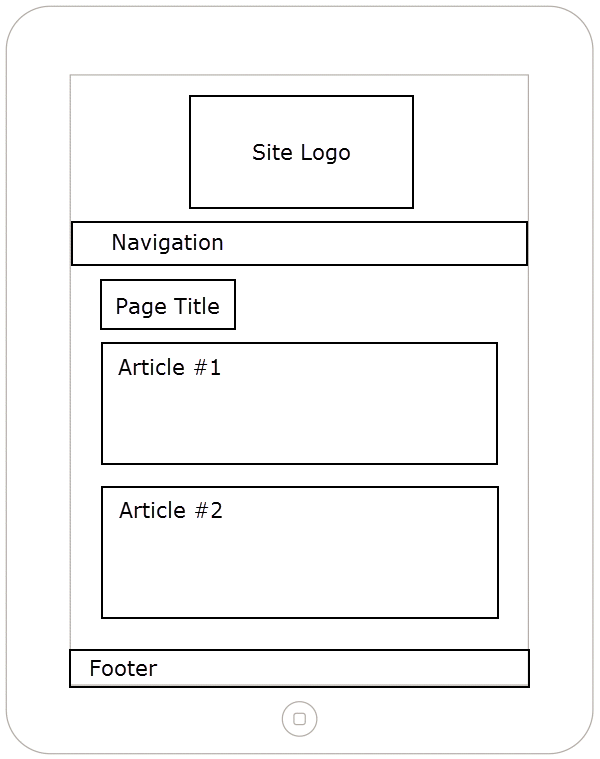
Responsive Sketches
Desktop/Laptop
Tablet - Portrait Mode
Tablet - Landscape Mode
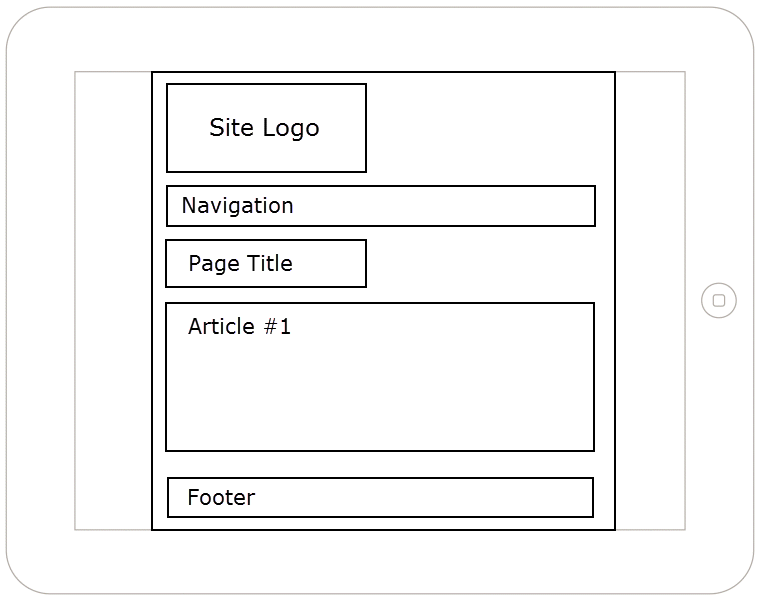
Mobile - Portrait Mode
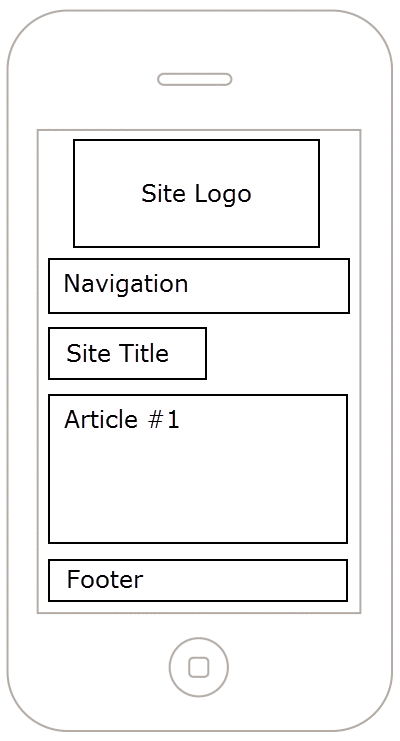
Mobile - Landscape Mode